SystemMen - How to disable Nginx test page in CentminMod? By default, when you install CentminMod, it will create a Nginx test page.
When you access the server’s IP address on the browser, it will display the HTML test page of CentminMod.
Is this good? Let’s take a look.
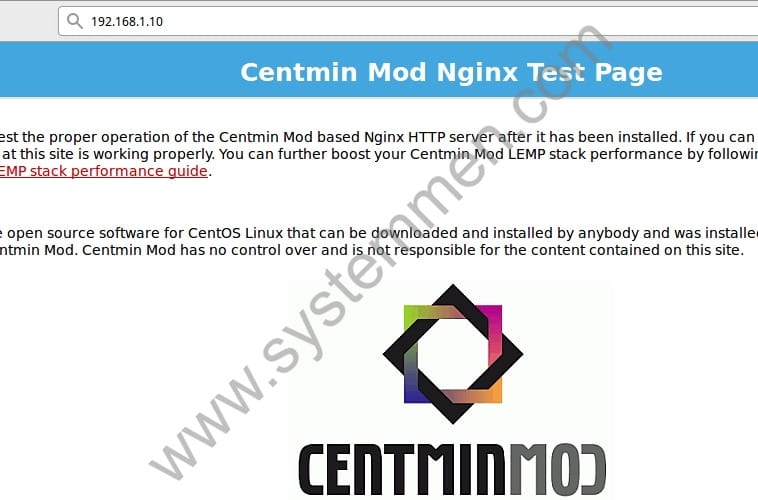
Why must disable Nginx test page in CentminMod?
With the experience of operating Linux server systems, I have worked with many different Linux systems.
To secure Linux servers, system administrators like me must hide information about the system. Make it hard to identify.
Hackers who want to attack a system will try to gather as much information about the target as possible.
And if you leave this page to Nginx test page, hackers can easily realize that you are using CentOS server and are using CentminMod to manage it. Hackers can rely on the vulnerabilities of CentminMod to exploit your server.
Therefore, we must disable it from the internet environment.
How to disable Nginx test page in CentminMod
First, you need to know where this page is configured in the server.
The Nginx test page is located in:
/usr/local/nginx/html/index.html
The vhost configuration file of test page in:
/usr/local/nginx/conf/conf.d/virtual.conf
After knowing where it is, we will now start the job.
Note: First, you need to create your website on CentminMod server first, use Let’s Encrypt as much as possible.
Recommended Reading: How to use Let’s Encrypt SSL in CentminMod
Next, we delete the virtual.conf configuration file.
rm -f /usr/local/nginx/conf/conf.d/virtual.conf
And then, create a file:
nano /usr/local/nginx/conf/conf.d/virtual.conf
With the following content:
server {
listen 80 default_server;
listen 443 ssl default_server;
server_name _;
ssl_certificate /usr/local/nginx/conf/ssl/yourwebsite.com/yourwebsite.com.crt;
ssl_certificate_key /usr/local/nginx/conf/ssl/yourwebsite.com/yourwebsite.com.key;
return 444;
access_log /var/log/nginx/localhost.access.log combined buffer=256k flush=5m;
error_log /var/log/nginx/localhost.error.log error;
location /nginx_status {
stub_status on;
access_log off;
allow 127.0.0.1;
#allow youripaddress;
deny all;
}
}
Look at the line return 444. Why is that?
I have encountered a case where a hacker took advantage of the vulnerability of server_name in web server Nginx to list the websites in that server.
Therefore, with the above configuration, if server_name is not configured in the CentminMod server. When accessing, you will get 444 code instead of randomly accessing the websites in the server.
And finally, you reload the Nginx configuration.
service nginx reload
Conclusion
Personally, I think you need to disable Nginx test page in CentminMod. This helps your server becomes safer against hackers. Try to hide your system as much as possible.
«« How to remove demodomain.com in CentminModIntroduction to InfluxDB time series database »»

Thanks for sharing. However, is this best practice all the way?
I mean — why not just disable / replace the default index page?
Also the conf file provided ought to be explained a bit better IMO.
I suppose the domain reference (“yourwebsite.com”) should be replaced with an already installed domain via CMM. But what if more than one website on server — should those other domains be updated in the cert conf file as well or is one reference enough?
Anyway, I run CF as a proxy which is pretty standard for CMM and tried your solution. After disabling cf. instructions here the subdomain used for CMM setup obviously displays a 503 error page. Should this not be handled more eloquently at the domain DNS level e.g. with a CF page rule permanent 301 redirect to other domain on server…?
Please share extended best practice as per your expeience.
Yes, if you have a proxy on the front, it will be very useful to hide this information without having to delete anything on CMM.
This article is from my work experience. actually its context is that you run a standalone CMM server and have no other layer of protection. So, we have to set it up a little bit.
We simply remove the default CMM information page (because it is not necessary when it works in practice). And with the Nginx conf file (return 444), the configuration is quite simple, it only returns code 444 with requests to domains not declared in the CMM server.
Many thanks for your comments. Please continue your suggestions.